



coScene Data Security Solutions
coScene Data Security Solutions
coScene Data
Security Solutions
Committed to Providing Secure, Transparent, Trustworthy, and Traceable End-to-End Data Services for All Users
End-to-End Data Encryption
End-to-End Data Encryption
End-to-End Data Encryption
Ensuring Data Link Security,Encrypting both internal and external communication links to safeguard the security and integrity of user data transmission, while strictly following the "Zero Trust" security principle.
Ensuring Data Link Security,Encrypting both internal and external communication links to safeguard the security and integrity of user data transmission, while strictly following the "Zero Trust" security principle.
Encryption & Authentication
We implement advanced encryption measures for every connection, utilizing protocols such as TLS 1.2, SSH-2, and IPSec to provide an impenetrable security barrier for data transmission. These protocols not only ensure data security during transmission but also guarantee data integrity.
Digital Certificates
coScene uses secondary CA certificates issued by globally leading enterprise digital certificate providers (such as DigiCert), ensuring that our connection identity validation and data encryption are at the forefront of global standards, offering the highest level of security for our customers.
Continuous Evaluation
Our professional team regularly evaluates and reviews the connections we use, ensuring that the selected encryption algorithms and key validation methods always align with current best security practices.
Security Monitoring & Response
We implement continuous security monitoring for critical tools like OpenSSL. Once a known vulnerability is detected, we can quickly respond and deploy necessary security patches, ensuring that our software and systems remain at the forefront of industry security standards.

Encryption & Authentication
We implement advanced encryption measures for every connection, utilizing protocols such as TLS 1.2, SSH-2, and IPSec to provide an impenetrable security barrier for data transmission. These protocols not only ensure data security during transmission but also guarantee data integrity.

Digital Certificates
coScene uses secondary CA certificates issued by globally leading enterprise digital certificate providers (such as DigiCert), ensuring that our connection identity validation and data encryption are at the forefront of global standards, offering the highest level of security for our customers.

Continuous Evaluation
Our professional team regularly evaluates and reviews the connections we use, ensuring that the selected encryption algorithms and key validation methods always align with current best security practices.

Security Monitoring & Response
We implement continuous security monitoring for critical tools like OpenSSL. Once a known vulnerability is detected, we can quickly respond and deploy necessary security patches, ensuring that our software and systems remain at the forefront of industry security standards.

Encryption & Authentication
We implement advanced encryption measures for every connection, utilizing protocols such as TLS 1.2, SSH-2, and IPSec to provide an impenetrable security barrier for data transmission. These protocols not only ensure data security during transmission but also guarantee data integrity.
Digital Certificates
Continuous Evaluation
Security Monitoring & Response
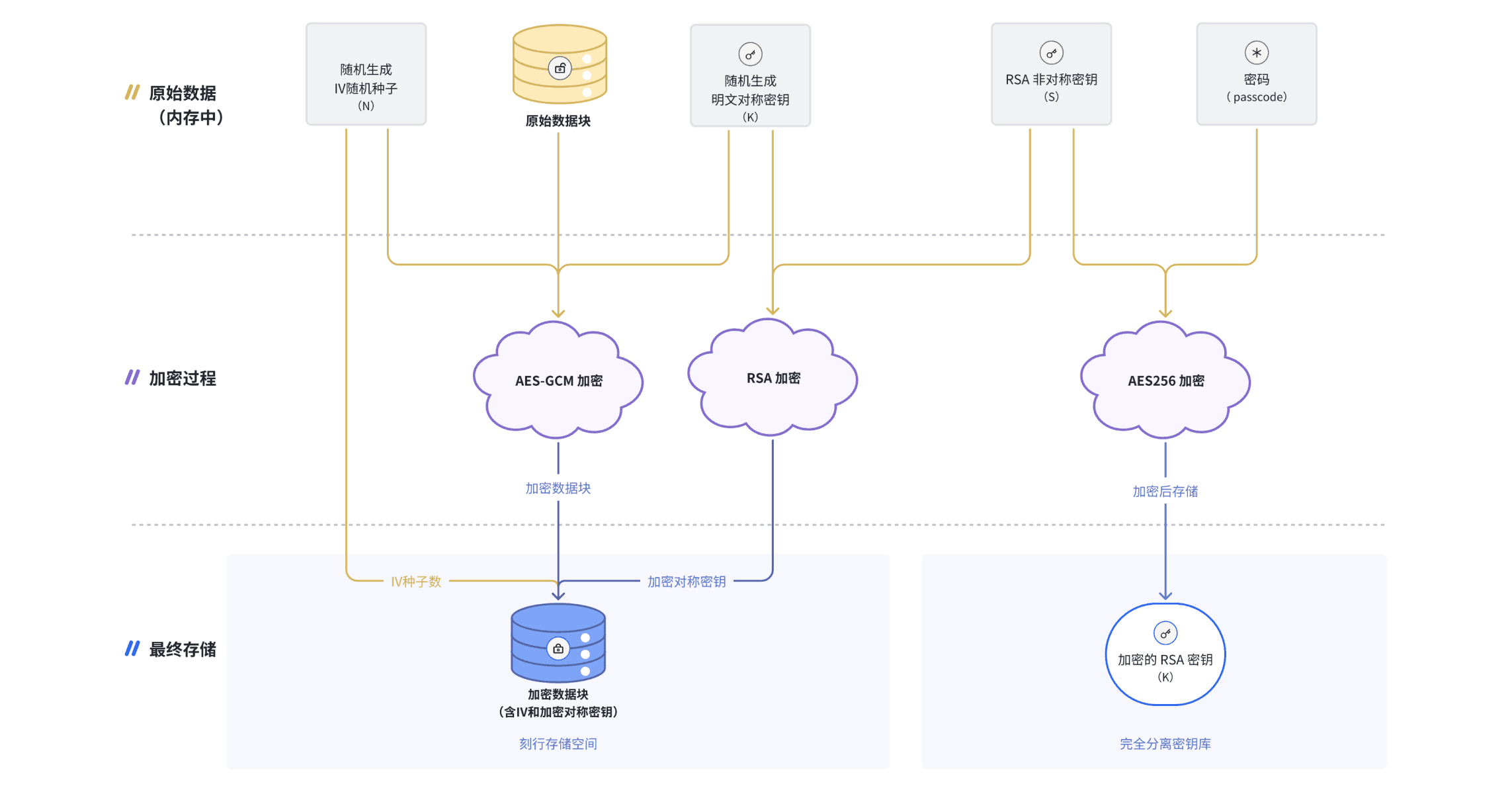
Encrypted Data Storage
Encrypted Data Storage
01
User Metadata and Structured Data
Data Protection First, with Full User Control.
On the coScene platform, we prioritize the protection of user-generated data. This includes, but is not limited to, sensitive data such as user configuration details, transaction information, and audit logs. For example, customized event fields, user events, recorded raw information, and activity logs are strictly managed and isolated based on each organization's requirements. We ensure that users can fully export and delete their data at any time, maintaining complete control over their information.




02
User Files and Binary Data
Data Encryption Ensures Privacy, with Secure and Worry-Free Key Management.
The coScene platform implements end-to-end encryption for all user-stored data. This ensures that even in extreme cases—such as hackers bypassing access controls to retrieve data from storage media—the encrypted data remains unreadable. Without the corresponding decryption key, the data cannot be exploited. Additionally, the keys themselves are strictly protected within the memory of the data services.
03
Implementation
Static Encryption Prevents Data Leaks—See Security Plan for Details.
The coScene platform enforces static encryption on all stored data, effectively preventing potential data breaches in case of unauthorized access or compromise in object storage. For more details on coScene's static data encryption process, please refer to our coScene Data Security Plan.

Access and permission isolation
Access and permission isolation
Access and permission isolation
Fully Transparent Logs and Activity Records

coScene is committed to providing industry - leading regulatory standards and levels of transparency. We enable users to easily monitor and review system activities by providing a series of user - friendly tools.
These tools include but are not limited to:
User behavior tracking
Records every step of user operations on the platform to ensure the traceability of operations.
Event operation records
Records the operation history of all events in detail for easy problem tracking and analysis.
Data operation records
Records every operation on the data to ensure the integrity and consistency of the data.
All this information is only visible to the administrators of the corresponding organizations of users. It can be queried through the operation interface of the coScene platform to ensure the visibility and transparency of operations.
Third-Party and Single Sign-On

coScene encourages users to adopt third-party or single sign-on methods. This not only simplifies the login process and improves user experience, but also reduces security risks related to password breaches by minimizing password usage. Additionally, any adjustments in the user’s existing organizational control structure are promptly reflected in the coScene platform, ultimately enhancing the overall security, reliability, and effectiveness of the system.
Role-Based Access Control (RBAC)

The coScene platform comes with a powerful role-based access control (RBAC) system, which grants administrators precise control over access to specific resources at multiple levels, including organization, repository, and project. This system meets the complex data access management needs of businesses of varying sizes and requirements.
Active Auditing Logs with On-Demand Queries

Anonymization and Intelligent Monitoring of Audit Logs
coScene platform anonymizes user audit logs to protect user privacy and data security. It also employs advanced pattern detection to deeply analyze logs, identifying potential data risks and abnormal behaviors.
Real-Time Alerts and Security Response
Once suspicious activities, such as downloads from non-whitelisted or uncommon network segments, are detected, our system immediately triggers an alert mechanism. These alerts are matched with cloud service provider levels and service level protocols, ensuring users receive timely notifications of potential security threats.
Internal Security Review
When necessary, coScene's internal security review team can quickly intervene to conduct detailed audits of suspicious behavior, ensuring security from both a programmatic and operational perspective, while minimizing risks from human error and external intrusions.
Fully Transparent Logs and Activity Records
Third-Party and Single Sign-On
Role-Based Access Control (RBAC)
Active Auditing Logs with On-Demand Queries
Fully Transparent Logs and Activity Records
coScene is committed to providing industry - leading regulatory standards and levels of transparency. We enable users to easily monitor and review system activities by providing a series of user - friendly tools.
These tools include but are not limited to:
User behavior tracking
Records every step of user operations on the platform to ensure the traceability of operations.
Event operation records
Records the operation history of all events in detail for easy problem tracking and analysis.
Data operation records
Records every operation on the data to ensure the integrity and consistency of the data.
All this information is only visible to the administrators of the corresponding organizations of users. It can be queried through the operation interface of the coScene platform to ensure the visibility and transparency of operations.

Fully Transparent Logs and Activity Records
Third-Party and Single Sign-On
Role-Based Access Control (RBAC)
Active Auditing Logs with On-Demand Queries

Fully Transparent Logs and Activity Records
coScene is committed to providing industry - leading regulatory standards and levels of transparency. We enable users to easily monitor and review system activities by providing a series of user - friendly tools.
These tools include but are not limited to:
User behavior tracking
Records every step of user operations on the platform to ensure the traceability of operations.
Event operation records
Records the operation history of all events in detail for easy problem tracking and analysis.
Data operation records
Records every operation on the data to ensure the integrity and consistency of the data.
All this information is only visible to the administrators of the corresponding organizations of users. It can be queried through the operation interface of the coScene platform to ensure the visibility and transparency of operations.

Encrypted Data Storage
User Metadata and Structured Data
01
Data Protection First, with Full User Control.
On the coScene platform, we prioritize the protection of user-generated data. This includes, but is not limited to, sensitive data such as user configuration details, transaction information, and audit logs. For example, customized event fields, user events, recorded raw information, and activity logs are strictly managed and isolated based on each organization's requirements. We ensure that users can fully export and delete their data at any time, maintaining complete control over their information.




User Files and Binary Data
02
Data Encryption Ensures Privacy, with Secure and Worry-Free Key Management.
The coScene platform implements end-to-end encryption for all user-stored data. This ensures that even in extreme cases—such as hackers bypassing access controls to retrieve data from storage media—the encrypted data remains unreadable. Without the corresponding decryption key, the data cannot be exploited. Additionally, the keys themselves are strictly protected within the memory of the data services.
Implementation
03
Static Encryption Prevents Data Leaks—See Security Plan for Details.
The coScene platform enforces static encryption on all stored data, effectively preventing potential data breaches in case of unauthorized access or compromise in object storage. For more details on coScene's static data encryption process, please refer to our coScene Data Security Plan.


Unlock Data Potential, Build the Data Flywheel


Unlock Data Potential


Unlock Data Potential, Build the Data Flywheel


contact@spatio.us
© 2025 Spatious Inc.
contact@spatio.us
© 2025 Spatious Inc.
contact@spatio.us
© 2025 Spatious Inc.